Achieving Zero Trust and Air-Gapped IaC in IBM Cloud With Schematics
IBM Cloud Schematics enables secure, automated, and policy-driven IaC deployments in air-gapped environments by enforcing zero-trust principles.
Join the DZone community and get the full member experience.
Join For FreeAs modern enterprises continue their journey toward cloud-native infrastructure, security and automation aren’t just nice to have; they’re absolutely essential. Particularly in regulated industries like finance, government, and healthcare, there's a growing need to deploy Infrastructure as Code (IaC) within isolated (air-gapped) environments while also embracing zero-trust principles.
In this blog, we’ll walk through how IBM Cloud Schematics can help you tackle these challenges head-on. We’ll explore how to securely provision IaC in isolated environments — while automating deployment and enforcing policy every step of the way. From air-gapped setups to zero trust enforcement, we’ve got you covered.
Understanding the Landscape
What Is an Air-Gapped Environment?
An air-gapped environment is a logically or physically isolated cloud setup with:
- No internet access
- No public gateways or NAT
- Manual or controlled data ingress/egress
- Used in highly secure, compliance-driven workloads
What Is Zero Trust in the Cloud?
Zero trust means:
- Never trust, always verify
- Authenticate every identity, workload, and device
- Apply least privilege access, even internally
- Continuously evaluate access context and risk
While air-gapped focuses on network isolation, zero trust focuses on identity and policy enforcement — and they can (and should) coexist in secure cloud deployments.
IBM Cloud Schematics: Terraform Automation, Built-In
IBM Cloud Schematics is a managed service that allows users to run Terraform IaC templates directly in IBM Cloud without installing Terraform CLI, managing state files, or worrying about provider versions.
Schematics is ideal for:
- Centralizing Terraform execution
- Applying IAM-based access control
- Managing IaC lifecycles securely from a GUI, CLI, or API
Why Use IBM Cloud Schematics in an Air-Gapped and Zero Trust Setup?
Centralized IaC Automation
Without managing infrastructure. Even in an air-gapped environment, Schematics can deploy resources into your private VPC using private endpoints. Terraform binaries can also be used from the local repository using the Schematics agents.
Zero-Trust Enforcement With IAM and Trusted Profiles
Trusted profiles are used to bind Terraform execution to a specific identity or trusted workload. Context-aware restrictions (CBR) policies are used to enforce the least privilege.
Securely Deploy into Air-Gapped VPCs
Schematics can access internal VPC resources via private endpoints. Schematics helps host your Terraform modules and provider binaries in private Git repos and mirrors. Schematics agents support custom provider configuration using .terraformrc.
Auditing, Compliance, and Logging Built In
Schematics integrates with IBM Cloud Activity Tracker for logging every action, Flow Logs on VPC for network observability, and Schematics workspace logs for execution traceability. These logs are essential for compliance audits and zero-trust continuous monitoring.
Seamless Integration With DevSecOps Pipelines
IBM Cloud ecosystem helps trigger Schematics from GitOps workflows, even within restricted CI/CD pipelines. It can use Secrets Manager to securely inject sensitive variables into IaC.
Key Components of the Architecture
Here is an example of what an air-gapped and zero-trust IaC stack looks like in IBM Cloud.
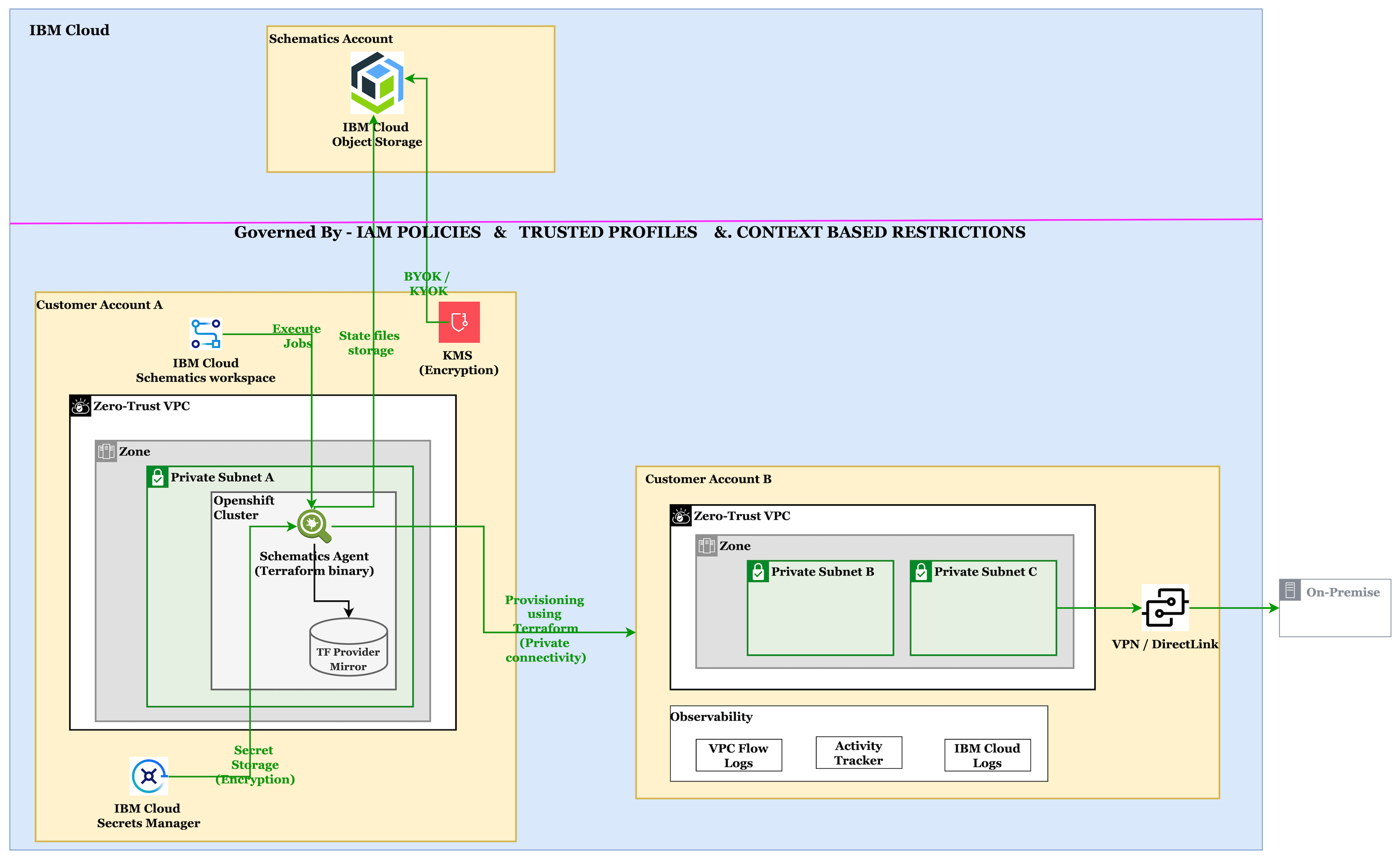
|
Component |
Purpose |
|
VPC with No Internet Gateway |
Isolates workloads with no public access |
|
Hosts VSIs, containers, and app services |
|
|
Access IBM Cloud services like COS, Key Protect securely |
|
|
Executes Terraform plans in a managed, policy-controlled plane |
|
|
Enforces workload identity, RBAC, and context-aware access |
|
|
For observability and audit logging |
|
|
VPN / Direct Link / Transit Gateway |
For secure communication from on-prem environments |
Implementing Air-Gapped, Zero Trust IaC in IBM Cloud
Step 1: Design Your Air-Gapped Network Topology
Create an IBM Cloud VPC with:
- No Internet Gateway (IGW)
- No NAT Gateway
- Private-only subnets
- No public-facing services or floating IPs
This forms the core air-gapped zone where resources are isolated from the internet.
Step 2: Set Up Private Endpoints for Cloud Services
Enable private service endpoints in your VPC for the following services:
|
Service |
Purpose |
|
For encryption key management |
|
|
For injecting secrets securely into Terraform |
This allows secure internal communication with IBM services without breaking the air gap.
Step 3: Configure IBM Cloud IAM With Zero Trust Policies
Set up resource groups and IAM access policies for:
- Users
- Service IDs
- Trusted Profiles (workload-based access)
- Use least privilege for all roles (e.g., only
Reader,Editor, orOperatoraccess for IaC). - Enable context-based restrictions (CBR)
This enables Zero Trust by ensuring all actions are identity-driven and continuously verified.
Step 4: Create IBM Cloud Schematics Workspace
- Create a Schematics workspace.
- Set the source to a private GIT repo (with SSH token or trusted profile access).
- Define variable values via Secrets Manager or encrypted inputs.
Schematics will serve as your automation control plane.
Step 5: Deploy with a Schematics Agent (Optional for Full Isolation)
If a full air gap is required:
- Set up a private Terraform provider registry.
- Deploy the IBM Schematics Agent inside the VPC.
- Connect it to the control plane using a trusted profile or secure bootstrap token.
- Use it to execute all Terraform commands inside the VPC while the plan/approval happens in the Schematics UI/CLI/API.
The agent runs within the air-gapped boundary, aligning with strict compliance requirements.
Step 6: Apply Policy as Code for Compliance
Use Open Policy Agent (OPA) to enforce:
- Naming conventions
- Resource size limits
- Region restrictions
- Network configurations
Integrating Policy as Code ensures your Zero Trust rules are enforced before deployment.
Step 7: Monitor and Audit
- Enable Activity Tracker for IAM and Schematics logs.
- Enable VPC Flow Logs to track network access.
- Use the Security and Compliance Center to scan deployed resources for violations.
These steps are essential for audit readiness, forensics, and continuous improvement.
Conclusion
Whether you're in regulated industries, combining air-gapped deployment with zero-trust enforcement gives you the best of both worlds. With IBM Cloud Schematics, you can deliver secure, zero-trust, air-gapped infrastructure with the speed of automation and the confidence of compliance.
Opinions expressed by DZone contributors are their own.

Comments