AWS CloudTrail Monitoring Using Event-Driven Ansible
Automate AWS CloudTrail event responses with Event-Driven Ansible. Learn how to monitor EC2 actions and trigger workflows for security, compliance, and efficiency.
Join the DZone community and get the full member experience.
Join For FreeAWS CloudTrail is a service that tracks everything happening in your AWS environment. It makes it easier to track activities like unauthorized access, configuration changes, or unusual behavior. It also supports compliance and auditing by maintaining a clear history of activity.
When we integrate CloudTrail with Event-Driven Ansible, we can automatically respond to these events in real time without manual intervention. This integration turns monitoring into action, helping teams keep their cloud systems secure, reliable, and easier to manage as they scale.
In this article, I will walk you through a practical example of integrating Event-Driven Ansible with AWS CloudTrail. You will learn how to use the ansible.eda.aws_cloudtrail module within Ansible Event-Driven Automation to monitor RunInstances (when an EC2 instance is launched) and TerminateInstances (when an instance is shut down and permanently deleted) events, and automatically trigger a workflow in response.
This automation can be extended to handle a wide range of security and operational events captured by AWS CloudTrail. It can run customized actions or workflows based on the specific needs and policies of the organization.
About the Module
The ansible.eda.aws_cloudtrail module allows Ansible Event-Driven Automation to directly poll and consume events from AWS CloudTrail without needing additional services. It enables real-time monitoring and automation by triggering Ansible playbooks in response to specific events, such as instance launches or IAM changes.
Demo Scripts
In this demo, I am running an Event-Driven Ansible script that monitors AWS CloudTrail events. To trigger the automation, I am launching and terminating EC2 instances through the AWS Console.
Once a matching event like RunInstances or TerminateInstances is detected, the script triggers a playbook that prints the event name and timestamp. This setup can be extended to perform more advanced automation based on the event details.
cloud-trail-demo.yaml
In the script below, we're monitoring CloudTrail events from the us-east-2 region and checking for new events every 5 seconds. It includes two rules — when event.CloudTrailEvent.eventName matches either RunInstances or TerminateInstances, the corresponding playbook is triggered automatically.
It will display the event name using the Ansible EDA variable, ansible_eda.event.CloudTrailEvent.eventName, along with the exact time it occurred using ansible_eda.event.CloudTrailEvent.eventTime, making it easy for users to identify which event was triggered and when.
- name: AWS CloudTrail Monitoring Demo
hosts: localhost
sources:
- ansible.eda.aws_cloudtrail:
region: 'us-east-2'
delay_seconds: 5
rules:
- name: Monitor RunInstances Events
condition: event.CloudTrailEvent.eventName == 'RunInstances'
action:
run_playbook:
name: run-instances.yml
- name: Monitor TerminateInstances Events
condition: event.CloudTrailEvent.eventName == 'TerminateInstances'
action:
run_playbook:
name: terminate-instances.ymlrun-instances.yml
---
- name: Print RunInstances debug message
hosts: localhost
connection: local
gather_facts: false
tasks:
- name: Print the RunInstance event details
debug:
msg: "Event Driven Ansible detected {{ ansible_eda.event.CloudTrailEvent.eventName }} at {{ ansible_eda.event.CloudTrailEvent.eventTime }}"terminate-instances.yml
---
- name: Print TerminateInstances debug message
hosts: localhost
connection: local
gather_facts: false
tasks:
- name: Print the TerminateInstances event details
debug:
msg: "Event Driven Ansible detected {{ ansible_eda.event.CloudTrailEvent.eventName }} at {{ ansible_eda.event.CloudTrailEvent.eventTime }}"Demo Screenshots
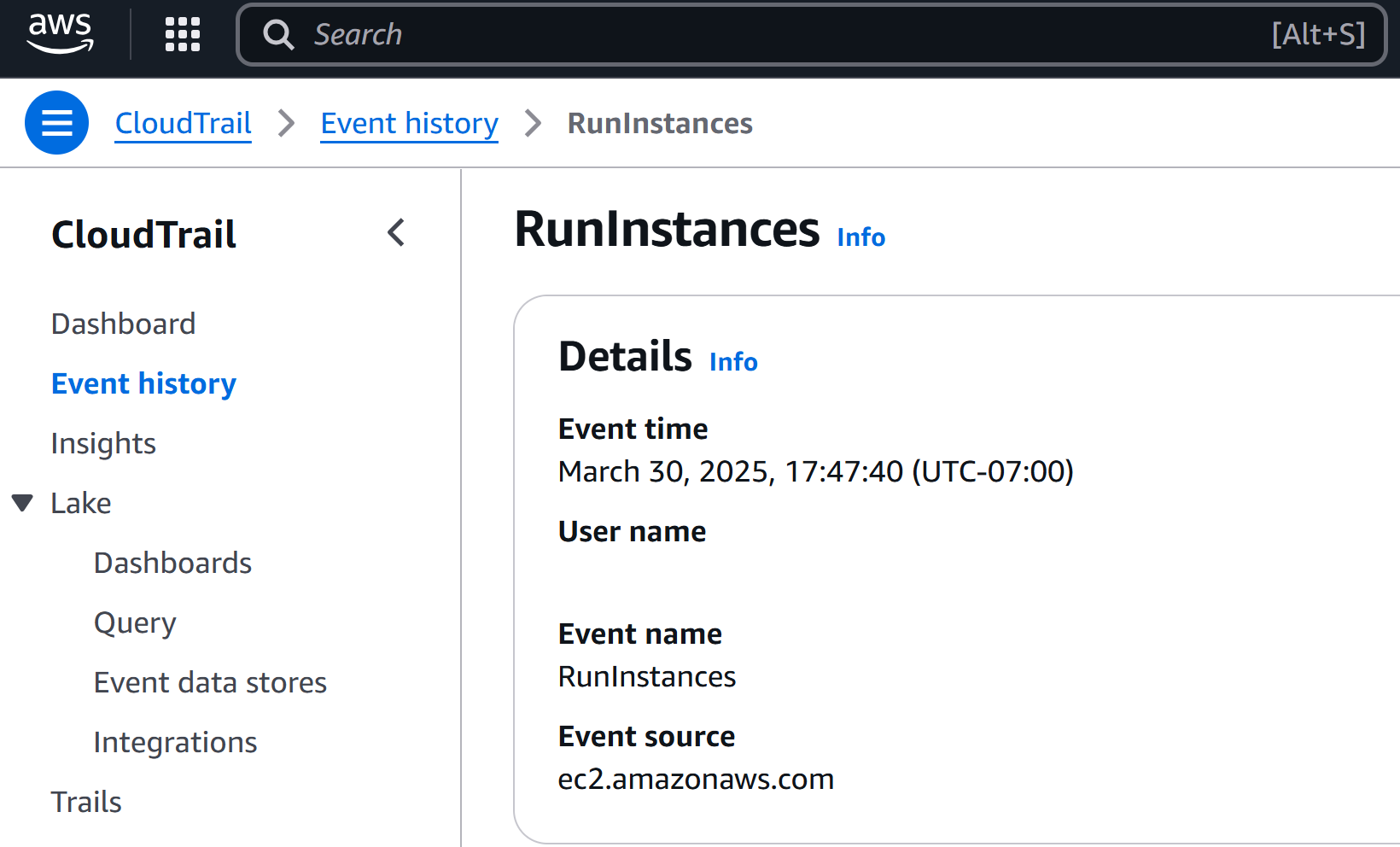
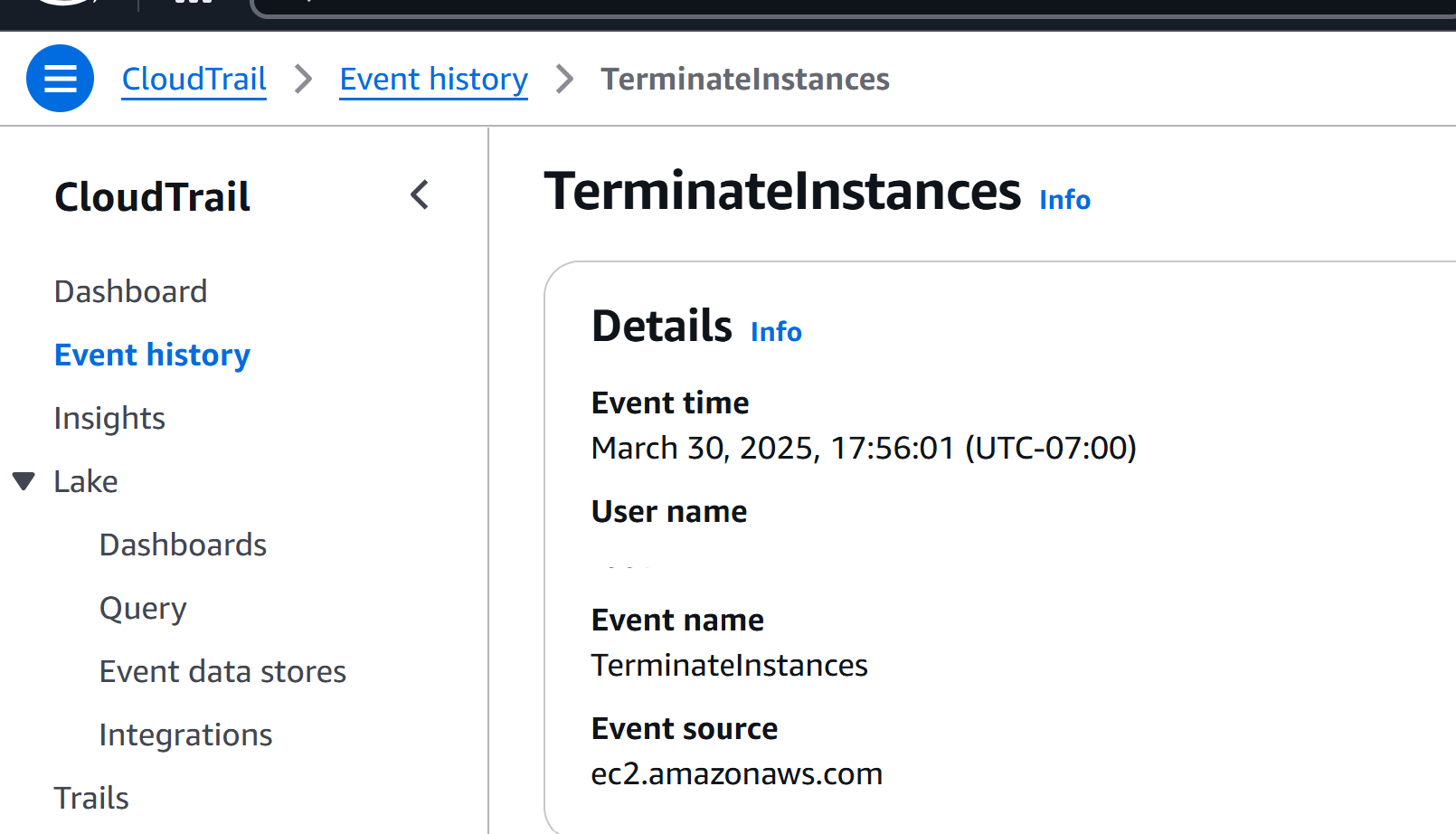
Below are the screenshots showing AWS CloudTrail event details for both the RunInstancesand TerminateInstances actions, which include important information like the event name, timestamp, and user identity.
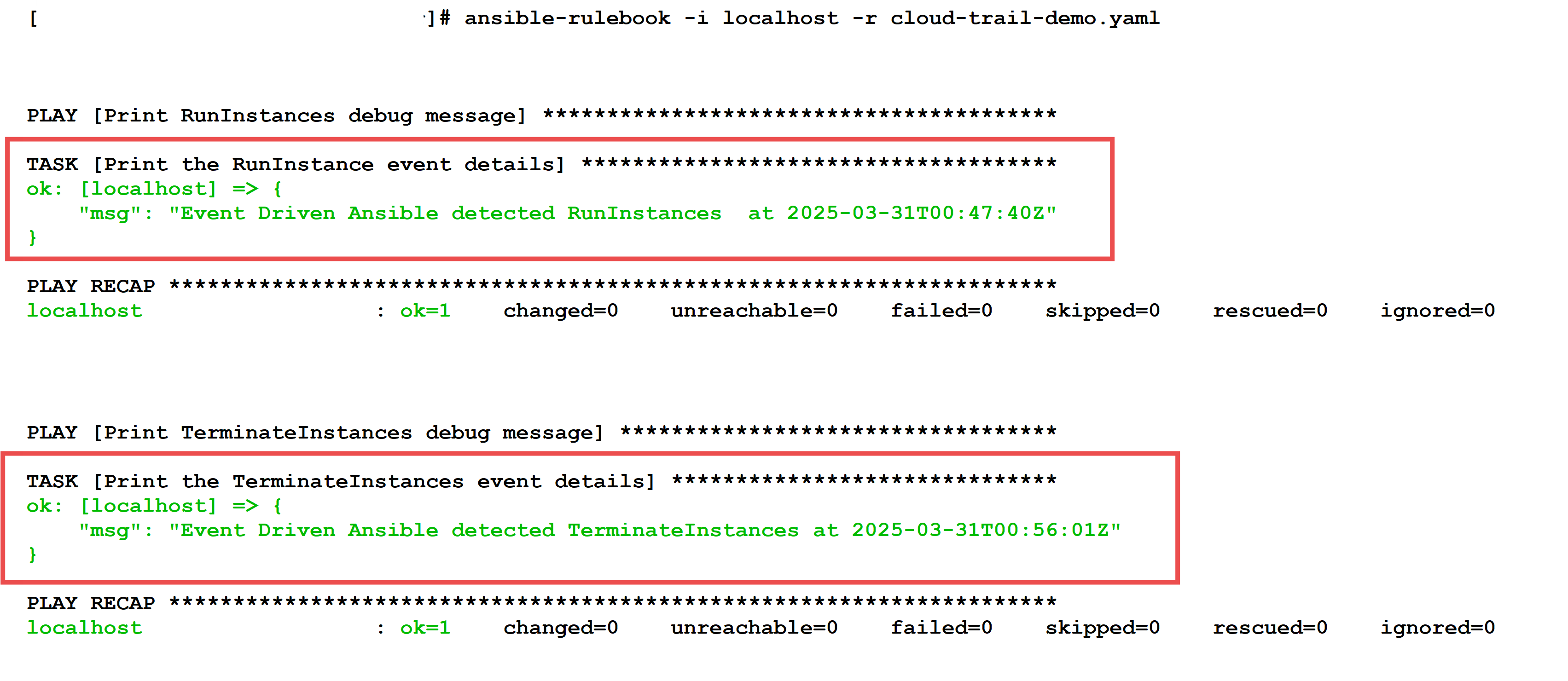
The final screenshot shows the Ansible Event-Driven Automation script running in a terminal, continuously monitoring these events. When a matching event is detected, the script will trigger the corresponding playbook to print the event name and the time it occurred in the terminal.
RunInstances
TerminateInstances
Monitoring Script
![Monitoring Script]()
Conclusion
In this demo, we explored how we can connect Event Driven Ansible with AWS CloudTrail using the ansible.eda.aws_cloudtrail module to automate actions based on real-time AWS events. We tracked events like launching or terminating EC2 instances and automatically ran playbooks in response.
This integration not only reduces manual effort but also enhances security, compliance, and operational efficiency. With further customization, it can be extended to support a wide range of cloud automation use cases tailored to organizational needs.
Note: The views expressed on this blog are my own and do not necessarily reflect the views of Oracle.
Opinions expressed by DZone contributors are their own.

Comments